Autrzn
SP is neutral to any identity provider.
As long as SP is provided with a SAML token which matches the industry standards settings, it accepts the same .In SP you will get multi-auth web applications i.e supporting various authzn. providers.This will show up in the Login page.
For custom Access Denied page :
Central Admin -- default login page or you can specify URL for the page that u have made.
SP is always running the STS(single token service) under the covers for us.
you can change the classic mode authn to Claims mode using Powershell.
Claims Identities provider: i.e. AD. whos is saying the username/group and the password is correct.
Claims Provider:
Provides claims that are adding extra attributes/claims to the user SAML token based on business rules.depending on the token values u authrz
Claims provider tell SP : here is some info abt the current user and trust me its correct .
Here is the info abt the user and based on the database i will populate some claims.
Its like HTTP module/handler in .Net . once the identity provider says that this is Sujoy the SP calls all the custom claims provider/providers and in that code you can add claims(eg Manager/Member/Geaography) to what you call is a SAML token.
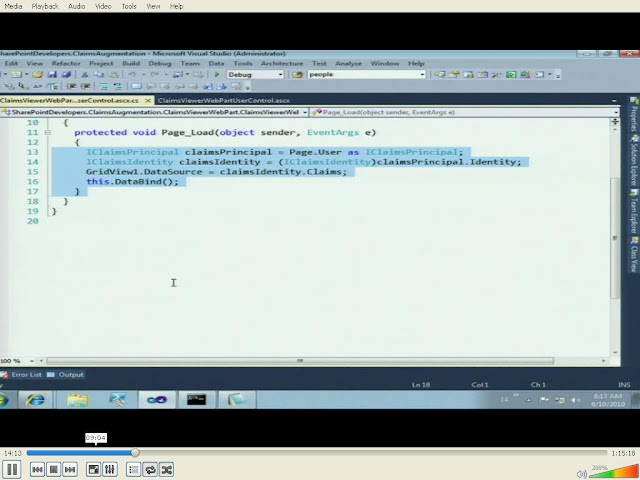
This is called claims augmentation.
AuthRiz.:
2 ways to accomplish the same :
People Picker
When u config claims using (FBA , Win Auth) these claims are going to show up in the ppl picker.So u can authrz depending on the claims.
The code that he has written generates 2 claims : manager, member claim.
So in can Authz according to what comes up as claim
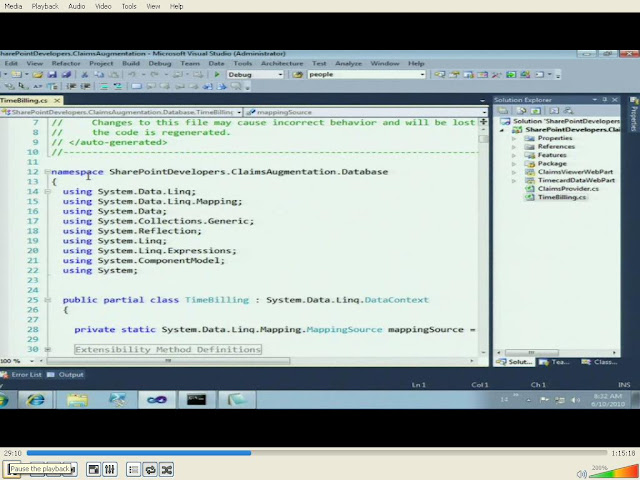
In the code there is Linq to SQL as SPMetal has been used for getting data from the database that contains user data .
The business req as shown in the video:
if the user comes in thru windows auth then the user is a manager
Else
the user comes in thru the FBA then the user needs to be verified against the db.i.e.member
 |
| Uses of Claims |
 |
| For Datagrid to display all claims that are there on the site |
2 scenarios ;
Scenario 1 :if its SP object (site/list /folder/item) then you can use the ppl picker.
Scenario 2 :However,if this is a webpart and the ppl picker is not best for that.(cant secure a webpart).here u can inspect claims for the current user and then render information accordingly.This is a authrz piece that will be v helpful.Uses custom code and then you can inspect the claims
Hence there are 2 things that claims provider can do :
1>Augment the token/claim and make that show in the people picker.
2>Claims Picker.
Steve Peschka -- blogs v usefull.
msdn.microsoft.com/en-us/library/ff699494.aspx
When some launches the ppl picker then the code goes thru the config file to find out the claims provder/provders that are registered/listed here.The claims are
picked up and added to the SAML token
FillResolve : When some 1 checks the check box infront of the name that is there in the people picker
FillSearch : when some types in the first letter in the searchbox of the claim(say m) and then hits search and the matching items come out.
CreateClaims() inbuilt method is used for the creation of claims .Helper methods should be used during coding.
Conclusions :
Provisioning permissions based on an attribute of the user, instead of on who the user is, opens many possibilities. It can mean, as it does in this scenario, that I do not care who you are. I do not care how you logged in. I do not care whether you are a Windows user
or a forms-based authentication user.
All I care about is who your favorite basketball team is.
Here is a classic problem from Microsoft Office SharePoint Server 2007 that still exists in SharePoint 2010—when I am at work, I log on to my SharePoint site by using my Windows credentials, Steve Peschka. But when I go home, I hit the site via our extra net and I must use forms-based authentication.
For our custom claims provider to support search, we must add support for the following properties and
methods of the SPClaimProvider class: SupportsSearch, SupportsResolve, FillSearch, FillResolve (the overload with SPClaim as an input parameter), FillSchema, and FillEntityTypes.
For Authnt/identity provider use the WIF classes.
=====================================================
User identity in Active Directory Domain Services (AD DS) is based on a user account. For successful authentication, the user provides the account name and proof of knowledge of the password. AD DS for account attributes and other information, such as group.
Claims-based identity is based on the user obtaining a security token
that is digitally signed by a commonly trusted identity provider and
contains a set of claims. Each claim represents a specific item of data
about the user such as his or her name, group memberships, and role on
the network Claims-based authentication in Windows is built on Windows Identity
Foundation (WIF), which is a set of .NET Framework classes that is used
to implement claims-based identity. Claims-based authentication relies
on standards such as WS-Federation, WS-Trust, and protocols such as
SAML.
If you select Claims-Based Authentication, SharePoint Server 2010
automatically changes all user accounts to claims identities, resulting
in a claims token for each user. The claims token contains the claims
pertaining to the user. Windows accounts are converted into Windows
claims. Forms-based membership users are transformed into forms-based
authentication claims. Claims that are included in SAML-based tokens can
be used by SharePoint Server 2010. Additionally, SharePoint developers
and administrators can augment user tokens with additional claims. For
example, Windows user accounts and forms-based accounts can be augmented
with additional claims that are used by SharePoint Server 2010.
Forms-based authentication is an identity management system that is
based on ASP.NET membership and role provider authentication. In
SharePoint Server 2010, forms-based authentication is available only
when you use claims-based authentication.
Secure Store Service(STS)
In Microsoft SharePoint Server 2010, the Secure Store Service replaces
the single sign-on (SSO) feature of Microsoft Office SharePoint Server
2007. The Secure Store Service is a claims-aware authorization service
that includes a secure database for storing credentials.
The Secure Store Service is an authorization service that runs on an
application server. The Secure Store Service provides a database that is
used to store credentials. These credentials usually consist of a user
identity and password, but can also contain other fields that you
define. For example, SharePoint Server 2010 can use the secure store
database to store and retrieve credentials for access to external data
sources. The Secure Store Service provides support for storing multiple
sets of credentials for multiple back-end systems.
Usage :
Microsoft Business Connectivity Services Can use Secure Store to map the user’s credentials to a set of credentials for an external system. You can either map each user’s credentials to a unique account on the external system or you can map a set of authenticated users to a single group account.
PerformancePoint Services Requires Secure Store if you want to configure an unattended service account for data authentication.
Similarly it can be used for the same in the PowerPivot for SharePoint 2010,Excel Services,Visio Services






No comments:
Post a Comment